WordPress is a powerful tool that allows you to create a website or blog both easily and to your exact specifications. This doesn’t mean that it’s without its flaws, however. If you’re hoping to get more out of WordPress, then there are a bunch of different extensions available for you to try from the Chrome Web Store. Here are five of the very best for you to have a look at. First on this list comes WordPress Theme Detector and Plugin Detector. This Chrome extension is great if you’re trying to get an idea of what else is possible with… More Info
Read More »Bluehost India Unveils Its New Campaign Focused On Helping SMBs Create Online Stores And Start Selling Digitally
Multilingual campaign aims to reach SMBs pan India to communicate the ‘EASE’ of creating e-commerce websites with Bluehost Bluehost is recommended by WordPress.org as one of the top trusted brands MUMBAI, India, April 22, 2022 /PRNewswire/ — Bluehost, a trusted web hosting provider specializing in WordPress, has unveiled a campaign targeting SMBs in India to help build online stores and start selling online. The multilingual campaign will be run in English, Hinglish and 3 other Indian languages (Kannada, Tamil, Telugu) across multiple media channels. It comprises two films showcasing… More Info
Read More »The WordPress Stack That Turns Designers Into One-Stop Web Agencies
Behind every web experience, there is a designer. Great designers are highly sought after for their insight into peoples’ expectations and their underlying assumptions about how things should work. Some web agencies prize their designers and grant them significant freedom to pursue innovative ideas. However, that’s not always the way things work. Often, technical demands and other obstacles get in the way, forcing designers to compromise on their ideas and change course. That’s why many web designers are looking for ways to bypass technical limitations and build… More Info
Read More »A Pared Back Web Fonts API May Land in WordPress 6.0 or Not at All – WP Tavern
Anyone who has been watching or participating in the development of the web fonts API can attest that it has been an emotional rollercoaster. At one point, it seemed to be a shoo-in for WordPress 5.9. Then, it was punted to the next release. Sure that it was landing once again, we find ourselves looking down the track, wondering just where the next dip or twist will take us. Over the weekend, I had a sense of dread. The WordPress 6.0 Beta 1 release last week felt premature. I am just as excited about the next major update as I have been about any before. There are tons of noteworthy… More Info
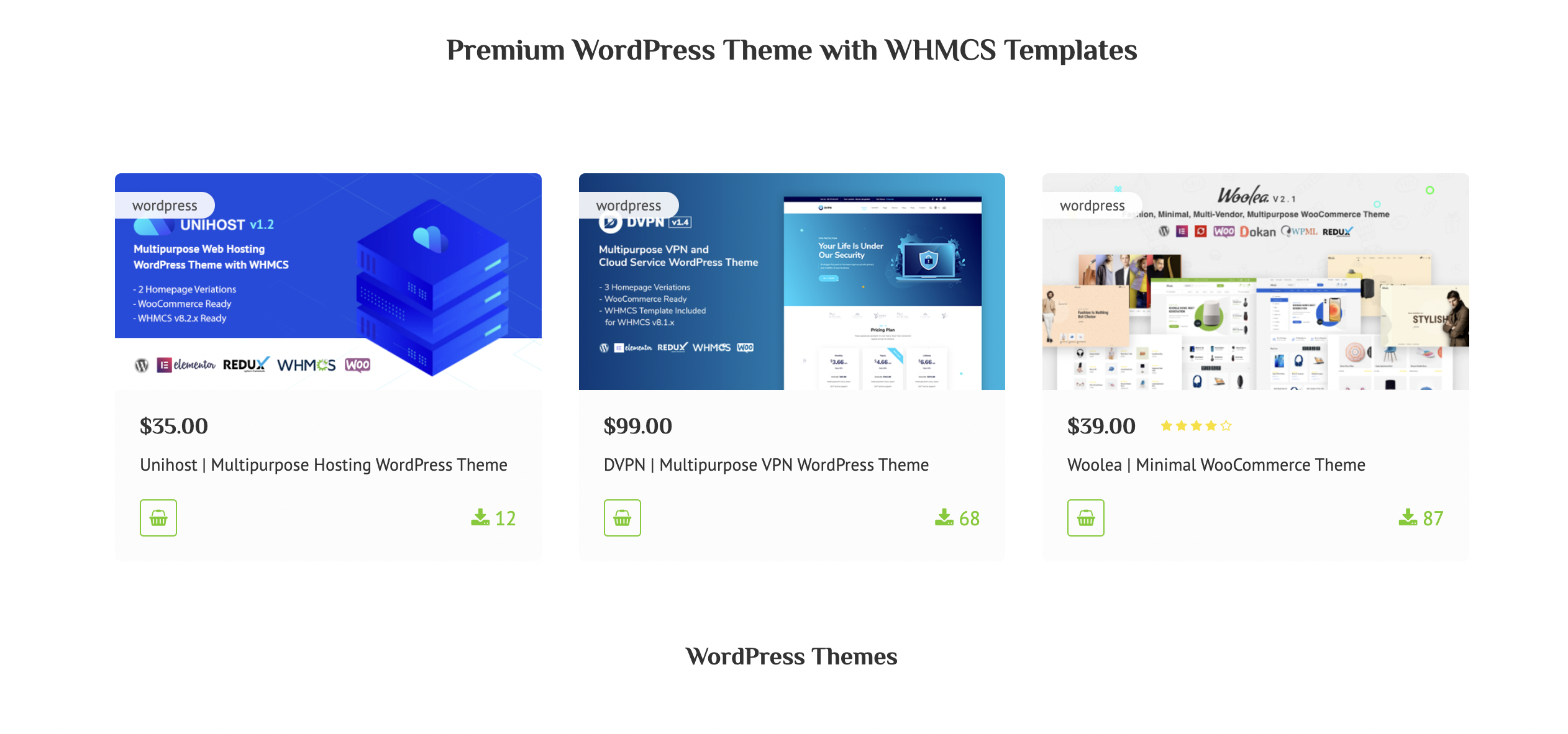
Read More »Best WordPress Themes Releases on ThemeLooks Marketplace
“Multipurpose Business WordPress Theme designed for All kinds of Creative Agency, Digital Acency, Design Agency, Online Business, Business Website etc.” By Designing with Love and Coding with Care, ThemeLooks is Here To Provide You The Best WordPress Themes and Plugins As Well As Fully Responsive Website Templates As one of the fastest-growing and outstanding Premium WordPress Themes and Website Template companies, Themelooks appreciates and understands the existence of small businesses. Themelooks has an exceptional and widespread reputation as a provider of theme and template… More Info
Read More »appsbd Launched Software License Manager for WordPress
“Elite Licenser by Appsbd is a WordPress plugin for any type of product licensing” Smartly Manage Your Product Licensing by Protecting Unofficial Usages of Software and Products and Control the Use, Activation of Software, Plugins, Themes, Apps, etc. Elite Licenser by Appsbd is a WordPress plugin for any type of product licensing. Furthermore, it manages product updates, auto-generates license code, is integrated with Envato licensing verification and has full license control. With its APIs, it can also be used by other applications. A single app controls all of your licenses. All… More Info
Read More »Dark mode switcher wordpress plugin finally here on themelooks marketplace
“Dark Mode Switcher For WordPress” Give Your Eyes A Treat by Enabling Dark Mode on Your WordPress Website for Having An Eye-soothing Experience DarkLooks | Dark Mode Switcher For WordPress is an excellent plugin that will turn your website viewing appearance into dark mode. It’s a must-use plugin for your WordPress site to give your eyes a break from extra lighting. Enabling/disabling the dark mode on your site will be done and dusted with just a simple click. ThemeLooks, the Software Company which is well known for providing the Best WHMCS Theme and Template announces the… More Info
Read More »Dark mode switcher wordpress plugin finally here on themelooks marketplace
“Dark Mode Switcher For WordPress” Give Your Eyes A Treat by Enabling Dark Mode on Your WordPress Website for Having An Eye-soothing Experience DarkLooks | Dark Mode Switcher For WordPress is an excellent plugin that will turn your website viewing appearance into dark mode. It’s a must-use plugin for your WordPress site to give your eyes a break from extra lighting. Enabling/disabling the dark mode on your site will be done and dusted with just a simple click. ThemeLooks, the Software Company which is well known for providing the Best WHMCS Theme and Template announces the launch of… More Info
Read More »Deals: Brizy Next-Gen WordPress Website Builder
We have a great deal on the Brizy Next-Gen WordPress Website Builder: Lifetime Freelancer Plan in the Geeky Gadgets Deals store. The Brizy Next-Gen WordPress Website Builder: Lifetime Freelancer Plan is available in our deals store for just $69, it normally retails for $299. Are you looking to build a website, but don’t have coding skills? Brizy is the next-gen website builder that anyone can use. No designer or developer skills required. Once you go Brizy, nothing else feels easy! With Brizy, you can build sites fast and easy and host them yourself. On top of main features like a… More Info
Read More »W3Main Upgrade Their Offerings To Deliver Complete WordPress Website Maintenance
Leading providers of WordPress website maintenance service, W3Main, upgrade their service offerings to offer comprehensive WordPress website maintenance for optimal security The team at W3Main, led by the passionate and experienced WordPress developer, T.C Barman, is staying true to the goal of ensuring that the online integrity of clients is not compromised. W3Main continues to upgrade their offerings to meet the diverse needs of businesses. In a related development, W3Main is currently offering a complete WordPress website maintenance service that comes without any extra cost. It is not… More Info
Read More »